
Bank robbers no longer need guns and masks like "Pretty Boy" Floyd did. See the progression of money scams through the 20th and 21st centuries. Then, learn what governments are doing to combat scams and what you can do to protect yourself.
Advertisement

Pickpockets are so smooth you won't guess they're out to get you. They use compassion and distraction to steal your wallet. Other schemers use similar emotional tactics, but on a much larger scale, as shown next.

Would you trust your money to this man? In the 1920s, many people did. Charles Ponzi took investors' money under the pretext of investing in International Reply Coupons. He had many imitators, but the man who did the most damage is shown next.

Bernie Madoff pulled off a wildly successful Ponzi scheme before things started to unravel and he confessed in 2008. Madoff's investment fraud stole from celebrities, banks, charities and even governments. Ponzi schemes are related to pyramid schemes, which you'll see next.
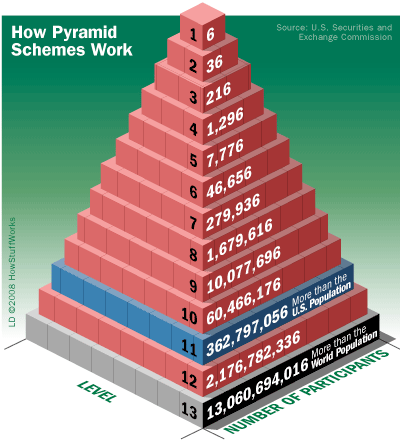
Pyramid schemes are different from Ponzi schemes in that participants don't just invest -- they must recruit more and more members and often sell products as well. All but those at the top will lose their investment. In the next few images, see how scammers started using technology in the 20th century. We'll begin with the telephone.
Advertisement

Long-distance scams have been around for many years. How many companies have called to sell you "better" long-distance rates? Phone scams pale in comparison to the next scam, though.

Identity theft can wreak havoc on your financial (and mental) well-being. And it's gotten worse since the Internet came along. See one of the most common scams to watch out for online.

In an effort to access your personal information, phishing scams try to lure you into giving out a password or social security number. See what one looks like next.
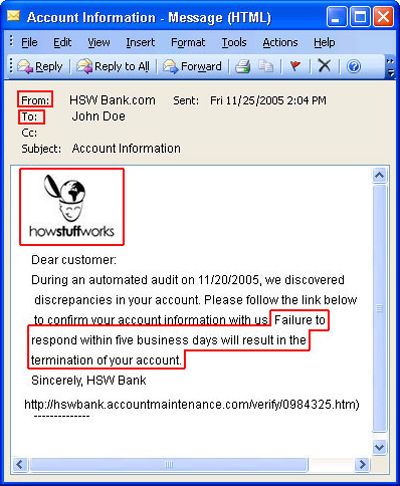
Phishing scams are designed to fool you into providing personal information, usually by responding to an email that appears genuine. Phishers often will try to imitate well-known and trusted websites.

In 2005, a Japanese scammer "phished" for identities with this fake Web site designed to fool people with its resemblance to Yahoo.com. Learn what eFencing is next.
Advertisement

The growth of online retail also brought about the rise of eFencing, which is the art of selling stolen goods to unsuspecting consumers at a hefty markup. They often use online auction sites like eBay.com. If you think that sounds bad, check out the sophisticated technology at work in the next scam.
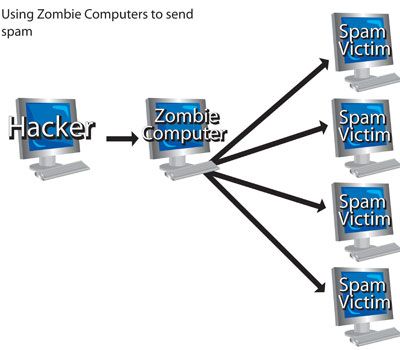
Zombie computers are those that have been taken over by crackers (malicious hackers), usually to send spam. Now, are you ready to see what the government is doing to protect you from these scams?

Unfortunately, clues are often harder to come by and less conclusive in white collar crimes than in traditional crimes. To deal with all the new scams cropping up, the United States government had to change some of its criminal laws.

The prevalence of money scams and white collar crimes caused the government to lay down the law -- punishments for white collar crime are much harsher than they used to be.

The FBI monitors e-mail scams and sends out alerts like this one. See one of the newest technologies used by banks and retailers next.
Advertisement
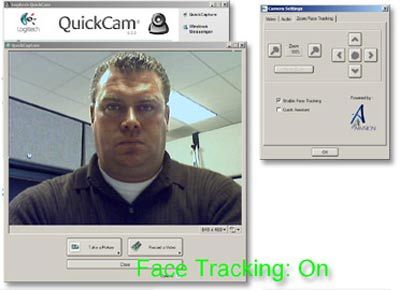
Banks are using facial recognition technology to prevent ATM and check cashing fraud. But the powers that be can only do so much. There are several methods that you can use to protect yourself.

Identity theft used to be as easy as picking up a discarded receipt. Now, most retailers only list the last four numbers of your account number. Still, it's a good idea to shred receipts. Next, see where you can spot identity theft or fraud as it's happening.

Monitoring your banking and credit card statements each month ensures that you see any suspicious charges in time to dispute them. Next, see one of the most common places scammers find your information.

Don't just trash your junk mail -- the garbage can is one of the most common places identity theft occurs. But what about protecting your information online?

Be very careful when using public computers. Don't allow the system to save any passwords. Still concerned and curious? Read more about identity theft, fraud prevention, or white collar crime.
Advertisement